Staying ahead of the latest threats is hard. Not understanding the technical jargon makes it harder. We define words to know, and share pro tips to keep you safe and protected.
These days, keeping your devices secure, data private, and online world safe from harm seems like a daunting task. While plenty of reliable solutions exist for desktop and mobile, knowing where you’re vulnerable can be difficult … especially if you’re not familiar with the jargon thrown around regarding the latest data breach.
At Your Technology Partner, we stay ahead of cybercriminals who look to profit by violating your right to freely and safely access the internet.
- Phishing. Used by cybercriminals to trick people into giving up sensitive information, phishing scams pose as emails from an organization or person you know. There is usually a link or attachment included, which it tries to get you to click so that you’ll unwittingly allow malware to download to your system. Sometimes phishing scams look indistinguishable from the sites they’re imitating, and they attempt to trick you into entering your password info.
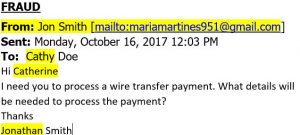
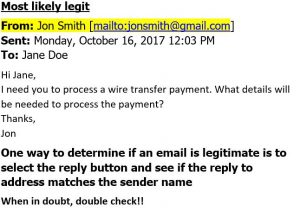
- Spear Phishing. Spear Phishing is an email-spoofing attack that targets a specific organization or individual, seeking unauthorized access to sensitive information. Spear-phishing attempts are not typically initiated by random hackers, but are more likely to be conducted by perpetrators out for financial gain, trade secrets or military information. Example of Spear Phishing email:
- DDoS attack. Attackers use DDoS (Distributed Denial of Service) attacks to render a network unavailable. They do this by overwhelming the targeted machine with massive requests from multiple devices. The target suffers a severely clogged bandwidth, and legitimate connections become impossible. These attacks are typically carried out by botnets (see above).
- Mobile banking Trojans. It looks like your trusted banking app, but that’s just an overlay. Underneath, a mobile banking Trojan tricks you into entering financial credentials and personal information. It can also gain administrative rights to intercept SMS messages, making it possible to record two-factor authentication codes as well.
- Open Wi-Fi. Encrypted connections protect you. Open Wi-Fi networks are unencrypted, which is why they’re risky. Anyone can create a fake hotspot and trick your device into joining it automatically. When you use open Wi-Fi without protection like a VPN (see tips below), anyone on that network can see the sites you visit, your log-in passwords, your financial and personal data, and more. Hackers often name their phony Wi-Fi networks after popular spots (like “Starbucks”), knowing that most devices automatically rejoin hotspots they’ve used in the past. Hackers can even redirect your unencrypted traffic, sending you to malicious sites.
- Botnet. A botnet (robot and network) is a network of devices infected by an attacker, and then used together to perform tasks such as carrying out DDoS attacks (see below), mining Bitcoins, and spreading spam emails. Nearly any device connected to the internet, including home routers, can be infected and pulled into a botnet without its owner ever noticing.
- Ransomware. Ransomware is malware that takes hold of your system and encrypts it, sometimes attacking individual files. Trying to access the encrypted files triggers a note that claims you are locked out until you make a payment (more than $600, on average). The messages sometimes appear to be from an official government agency accusing you of committing a cyber crime, which scares many into paying the ransom. Payment is often demanded in Bitcoins.
- Spyware. Spyware is malware used by hackers to spy on you, so they can access personal information, banking account details, online activity, and anything else they may find valuable. On mobile devices, spyware can know your whereabouts, read your text messages, redirect calls, and much more.
- WPA2. WPA2, the encryption standard that secures all modern wifi networks – has been cracked. An attacker could now read all information passing over any wifi network secured by WPA2, which is most routers, both public and private.
- Krack. The Krack Attack is a newly discovered internet security flaw. It’s a bug so vicious that it can cut through secured Wi-Fi networks in homes and businesses. If a hacker gains access through this type of attack, that person would have a front row seat to everything on your network. From your private chats on apps to baby monitors, if the device uses Wi-Fi, it can be hacked. The attack takes advantage of what’s known as “the four way handshake.” This process between a device and a router delivers a fresh, encrypted session every time you get online.
- Bad Rabbit. A new ransomware campaign has hit a number of high profile targets in Russia and Eastern Europe. It recently has hit targets in the USA. Dubbed Bad Rabbit, the ransomware first started infecting systems on Tuesday 24 October, and the way in which organizations appear to have been hit simultaneously immediately drew comparisons to the WannaCry and Petya
Tips to keep yourself safe and secure
While it may all sound daunting, employing a few simple strategies will keep almost everything from botnets to Trojans at bay. Here are our top tips:
- Install solid security software on every device. Avast Free Antivirus prevents malware from infecting your device, and also provides Wi-Fi Inspector, which scans your home router for vulnerabilities. All paid versions of Avast Antivirus feature Real Site, ensuring you reach the actual websites you want to visit, and prevents hijacking, thanks to an encrypted connection between your web browser and Avast’s own DNS server.
- Use strong and unique passwords. To generate hyper-secure passwords, use a password manager, like Avast Passwords, which comes free with Avast Free Antivirus. It also alerts you if your email address may have been included in a data breach so you can take action.
- Only download apps only from trusted sources. Also, use a smartphone antivirus like Avast Mobile Security, which blocks Trojans from entering and removes any that already have.
- Employ a virtual private network (VPN) if you plan to take advantage of free, open hotspots. A VPN—such as Avast SecureLine VPN—creates a secure, encrypted connection, protects your personal data and your privacy. With VPNs, you browse anonymously and your location is changed, helping to keep you from being tracked.
- Think twice before opening attachments, following links, or sharing sensitive info. Look closely at any email asking you for personal information. If you see a typo or incorrect logo, or anything that puts you in doubt, contact the sender (using a method other than replying to the email) to verify the contents before taking any action.
- To prevent ransomware from attacking your system, look into security software like Avast Internet Security, now with Ransomware Shield, which can be installed on all of your PCs.
- Call Your Technology Partner immediately if you suspect any threats to your computer.
Source: Avast and Your Technology Partner

Recent Comments